- PID
- 3081516
S2KLogin SSH VPN
- Award
-
- Shipping
-
- Payment
-
140+ Global Payments, trusted and secure payment provided by PayVerse.
Learn More
Detailed Description
Our goal is to provide an efficient and convenient security service to our clients. S2K login service is designed to be installed easily, uninstalled easily, and most importantly, to serve as a strong security agent for your servers. Media coverage has ensured that many people have heard or read about the tremendous number of security breaches that have occurred in the past few years at businesses such as Target, Neiman Marcus, Home Depot, J.P. Morgan Chase, Sony and Ashley Madison. IoT technology has become the center of many services and infrastructure of our lives, and most likely will be applied to more fields.
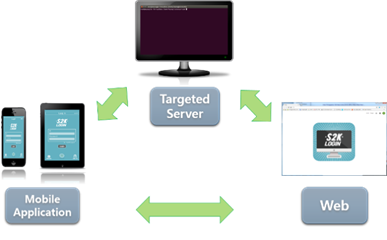
Businesses are trying to apply the technology to as many fields as possible, but are less concerned about how they protect the thousands of the devices from numerous security flaws. S2K SSH VPN solution has up to 7 layers of security (from the physical layer to the application layer), which have to be paired appropriately with one another in order to access to the targeted VM (or any connectible entity within the network). \
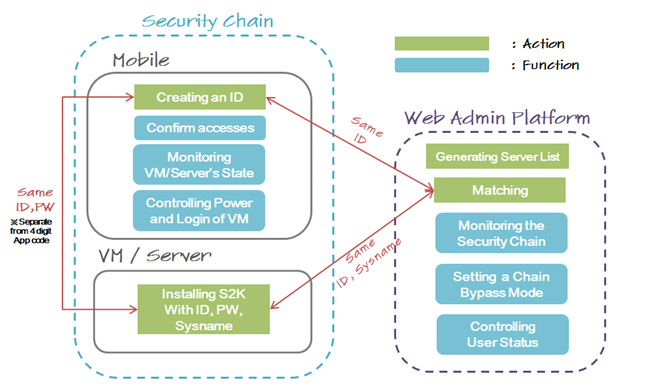
This secured solution guarantees that any unauthorized individual is not able to get into your protected server even though your UserID and Password leak out. In addition, our Web platform is designed to administrate the connections between users and servers conveniently.
Here is a picture briefly showing the overall structure of S2K security solition. A normal registration process is to be done in order of mobile, VM / Server, Web platform. However, for your convenience, if you register your ID first on the Web Platform and then sign up on your mobile, it will automatically work if you use the same ID. This user manual will focus primarily on the process starting with mobile sign-up. If you understand this procedure, the opposite procedure will naturally be understood.