- PID
- 3082921
S2K SSH VPN
- Award
-
- Shipping
-
- Payment
-
140+ Global Payments, trusted and secure payment provided by PayVerse.
Learn More
Detailed Description
PRODUCT DETAIL
1. Introduction
- S2KLogin SSH VPN securing your local (SSH) and remote UNIX logins lets you protect your
developers and source code against remote attacks on your production systems and other
critical networks. → S2KLogin SSH VPN to protect your SSH servers.
- Adding the extra tracking features onto the 2FA(2 Factor Authentication)system could gain
the company to activate the audit trails on each machine which would generate a large
amount of logs.
2. Detail explanation
Our goal is to provide an efficient and convenient security service to our clients. S2K login service is
designed to be installed easily, uninstalled easily, and most importantly, to serve as a strong security
agent for your servers. Media coverage has ensured that many people have heard or read about the
tremendous number of security breaches that have occurred in the past few years at businesses
such as Target, Neiman Marcus, Home Depot, J.P. Morgan Chase, Sony and Ashley Madison.
IoT technology has become the center of many services and infrastructure of our lives, and most
likely will be applied to more fields.
Businesses are trying to apply the technology to as many fields as possible, but are less
concerned about how they protect the thousands of the devices from numerous security flaws.
S2K SSH VPN solution has up to 7 layers of security (from the physical layer to the application
layer), which have to be paired appropriately with one another in order to access to the targeted
VM (or any connectible entity within the network).
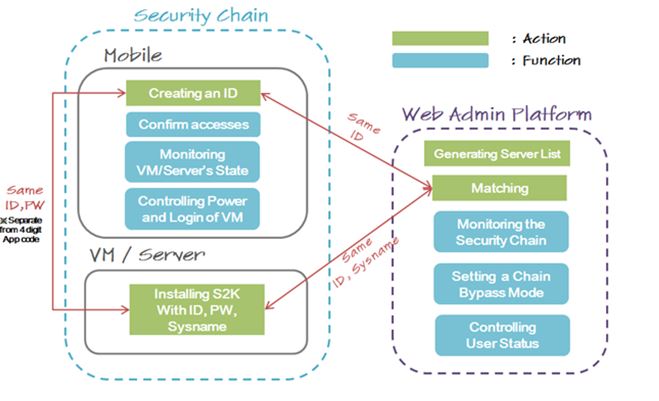
This secured solution guarantees that any unauthorized individual is not able to get into your
protected server even though your UserID and Password leak out. In addition, our Web platform
is designed to administrate the connections between users and servers conveniently.
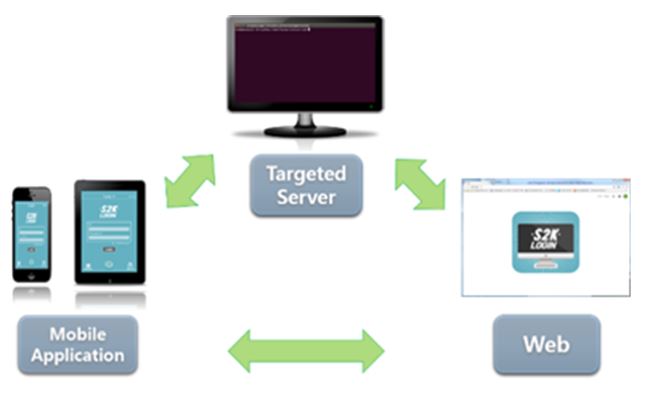
Here is a picture briefly showing the overall structure of S2K security solition. A normal
registration process is to be done in order of mobile, VM / Server, Web platform. However,
for your convenience, if you register your ID first on the Web Platform and then sign up on your
mobile, it will automatically work if you use the same ID. This user manual will focus primarily
on the process starting with mobile sign-up. If you understand this procedure, the opposite
procedure will naturally be understood.
3. Usage
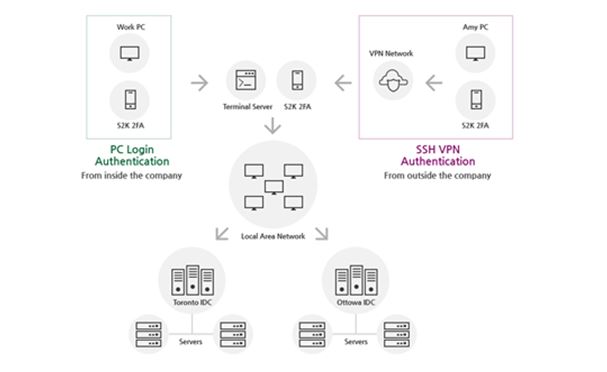
S2K SSH VPN Network Diagram
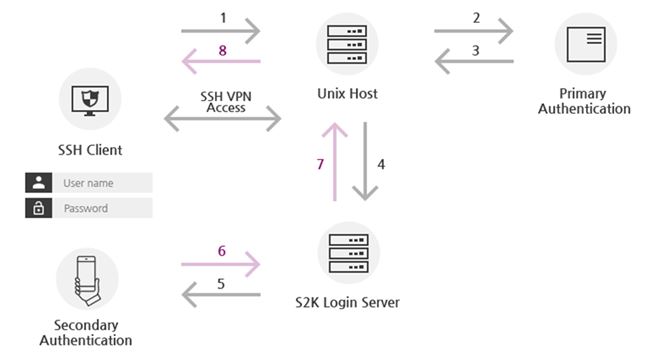
2FA(Two Factor Authentication) Precedure
[Feature]
- Password Free Login
- Easy User Interface
- Safety From Data Farming Websites
- Risk Based Authentication
- Be useful for companies that have a lot of traffic into their servers From SSH VPN access points.
- Protecting your developers and source code against remote attacks on your
production systems and other critical networks
COMPANY INTRODUCTION
[2009~2012]
1.Enterpreneurship Competition Main Award(Content Security Technologies)
2.Venture Company Acccreditation(Technology Guarantee Fund)
3.ISO 2009 Certification(Crebiz Certification)
[2013~2014]
4.Certified service technology transfer(ETRI) based on wearable devices.
5. 1 Room, 1 Company Enterprise Support Certificate(ETRI, open authentication technology)
6.Seoul Rising Star Enterprise Certification(Seoul Business Agency/Seoul, Korea Credit
Guarantee Foundation)
[2015~2016]
7.TTA V&V and GS Certified (Secure2Key)
8.Participation in seminars and demoday organized by the Financial Supervisory Service
9.MOB Service-Nonghyeop MOB Commercialization
10.Supply S2K Beacon Attendance Solution (Korea University)
11.Supply IoT Security solution (SKT Telecom)
● COMPANY VISION
“We will do our best to provide services, which are absolutely necessary and also beneficial
for people, with the highest standards of quality and usability on top of being aesthetically pleasing.”
● BUSINESS MODEL
- IoT Security
- S2K(Authentication Before Transaction Service) Technology Based Business




